
Seqrite
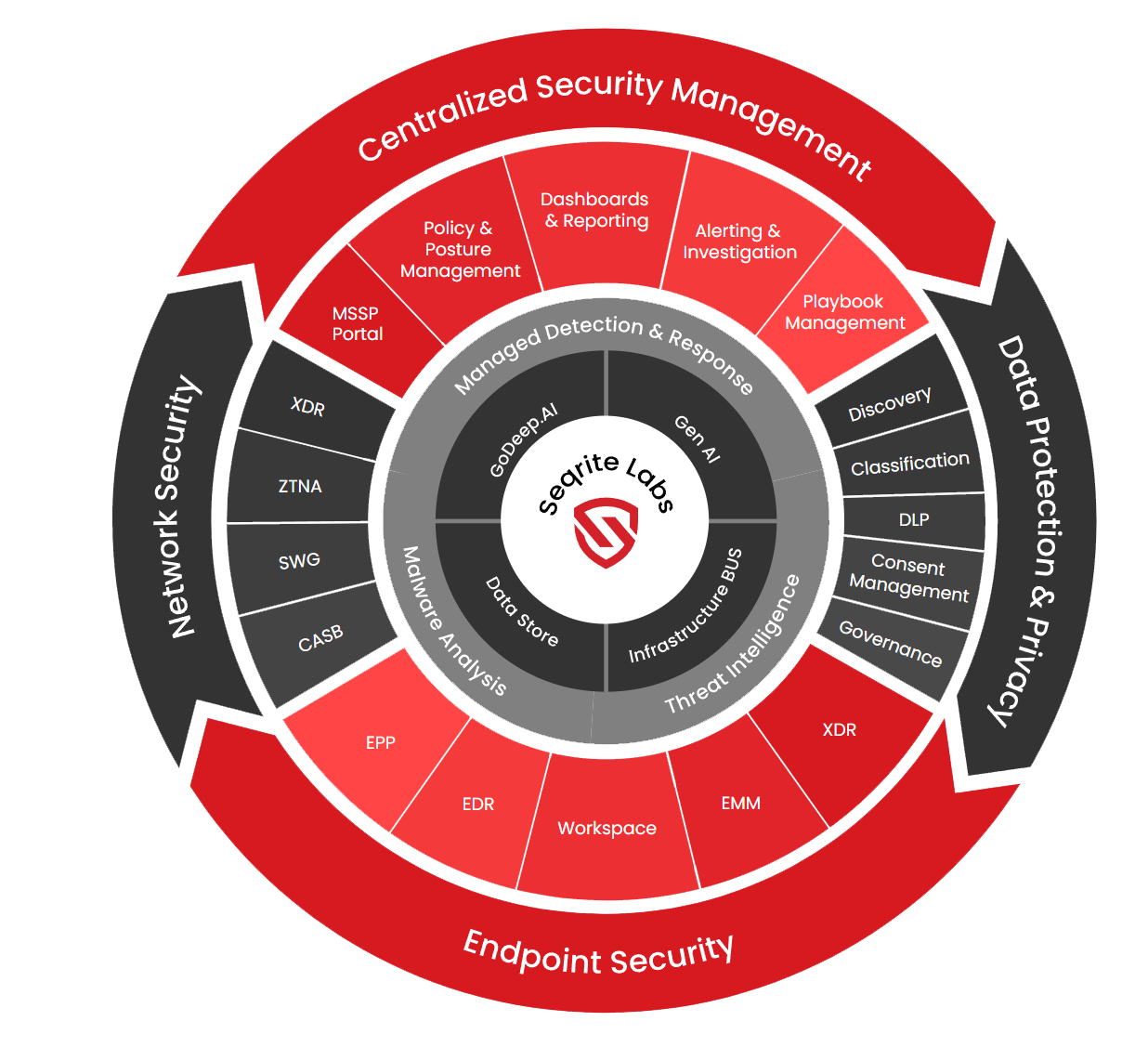
Seqrite transforms enterprise security with cutting-edge solutions designed to proactively detect, mitigate, and respond to evolving cyber threats. Seqrite ensures comprehensive protection across endpoints, networks, and cloud environments by leveraging AI-driven intelligence and automated security operations.
- Unparalleled Threat Detection and Response
- Risk-based Security Prioritization
- End-to-End Endpoint Protection
- Seamless Zero Trust Access & Identity Security
- Automated Incident Management and Compliance
Seqrite provides a holistic cybersecurity approach, ensuring organizations remain secure, resilient, and ahead of the threat curve.
Experience Robust Protection on a Single, Unified Platform
With AI-driven, multi-layered security, Seqrite offers robust protection across endpoints, networks, cloud applications, and mobile devices. Over 30,000 enterprises in 76+ countries trust Seqrite to secure their digital assets, ensuring an efficient and reliable investment.
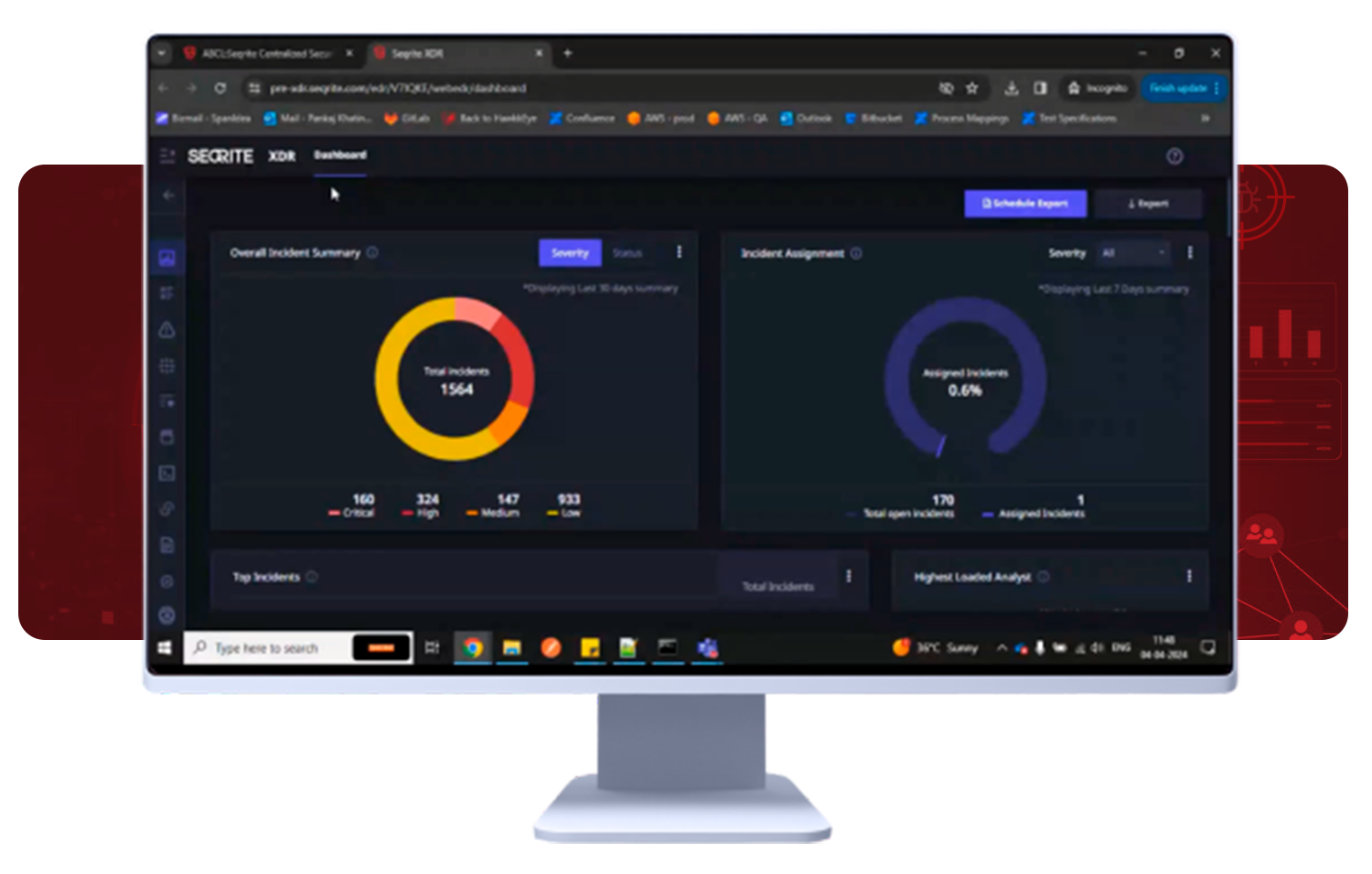
Extended Detection and Response (XDR)
An advanced incident response tool that centralizes, normalizes, and correlates data from multiple security products to deliver holistic protection against cyberattacks. It provides real-time cross-control-point protection, simplifying and strengthening security processes.
- Key Features:
- Automated threat hunting and remediation.
- Machine learning and behavior anomaly detection.
- Historical data search for missed IOCs.
- Incident and SLA management with 50% resource reduction
- Benefits:
- 24/7 active vigilance with ML and automation.
- Affordable price point with optimized storage algorithms.
- Comprehensive incident management and SLA definition.
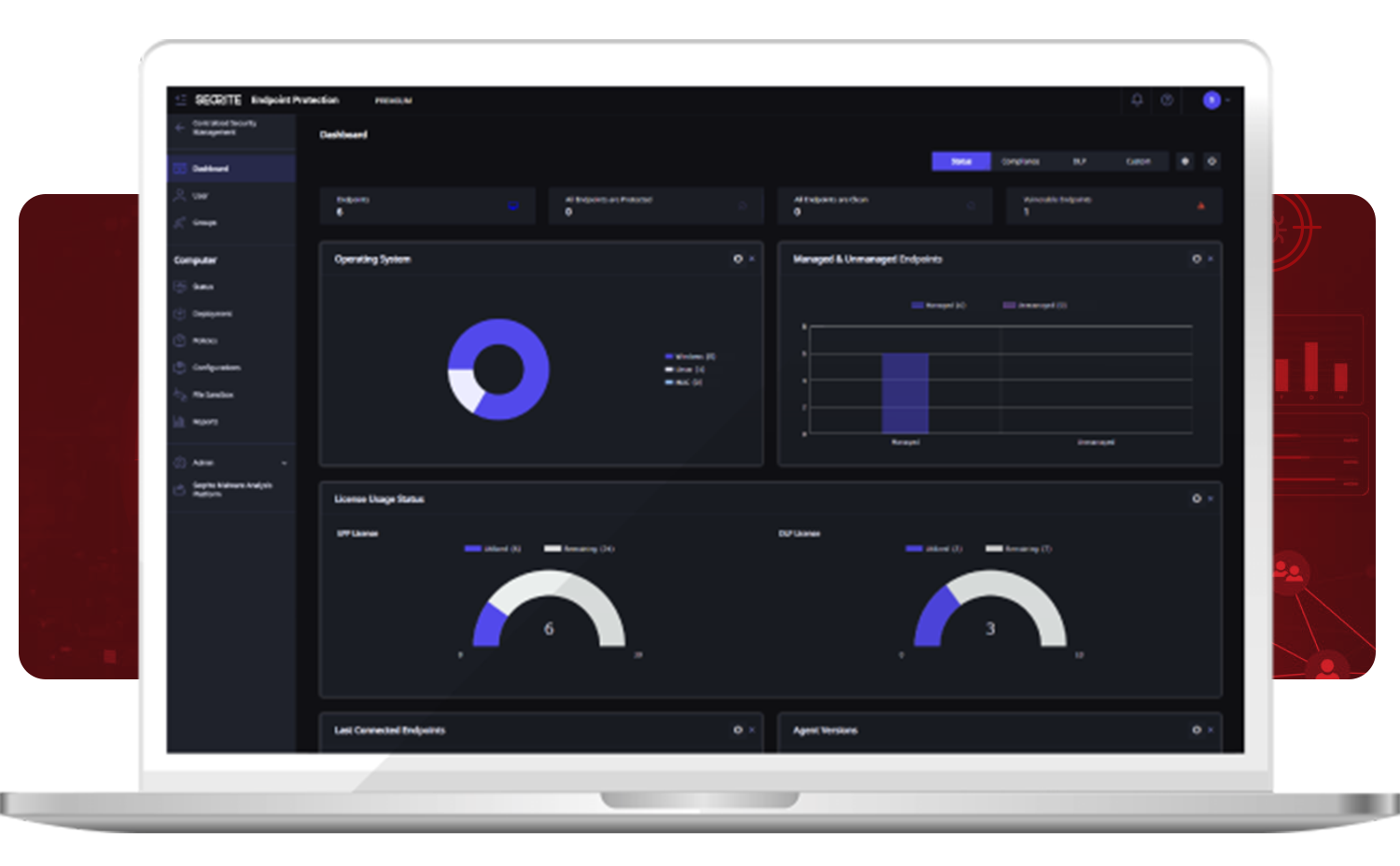
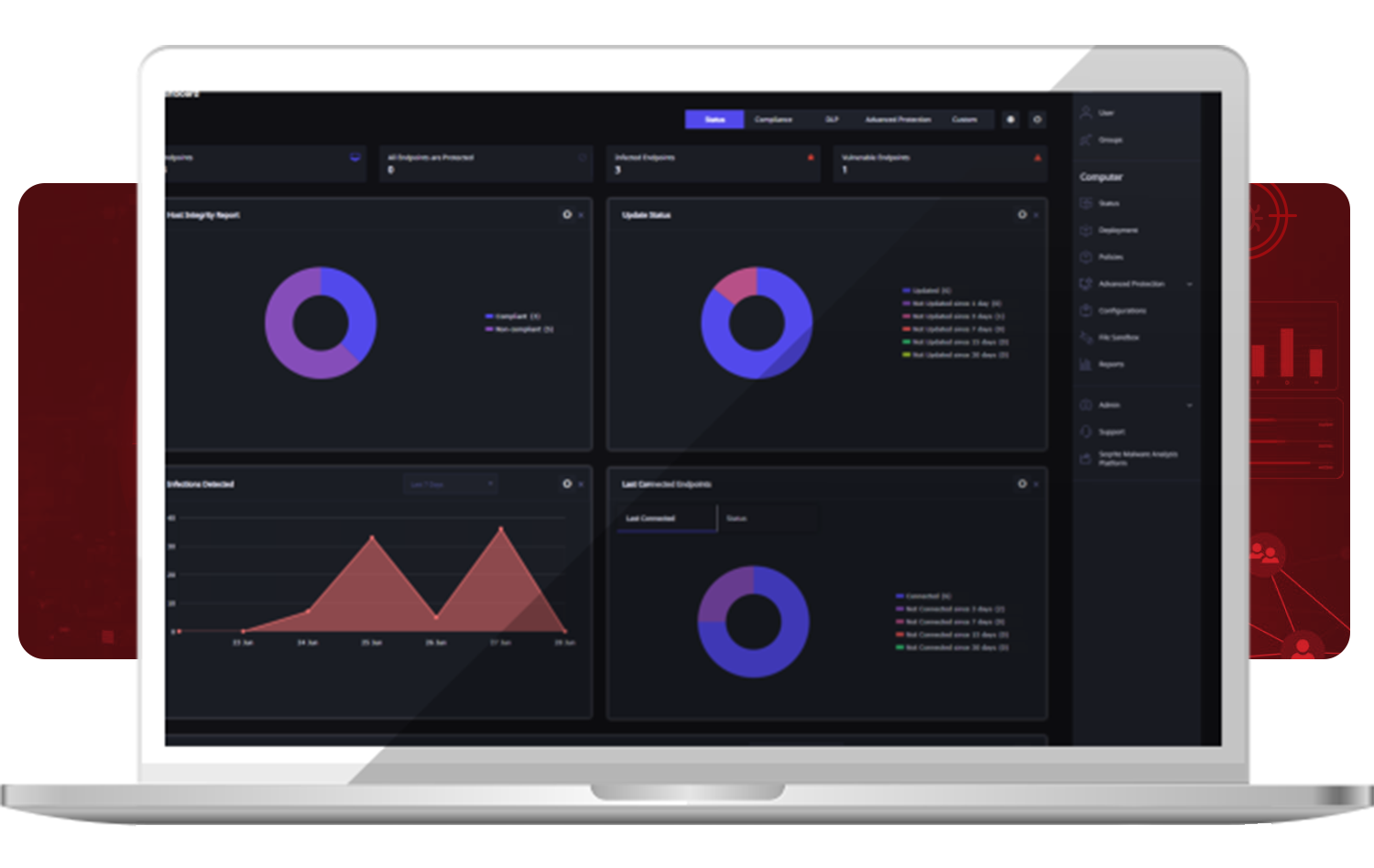
Endpoint Protection (EPP)
Comprehensive endpoint protection for workstations, laptops, and servers. It integrates innovative technologies like Anti-Ransomware, Behavioral Detection, and Endpoint Threat Hunting to protect against advanced threats.
- Key Features:
-
- Advanced Device Control, DLP, and Web Filtering.
- Vulnerability Scan and Patch Management.
- Centralized management and control with detailed dashboards.
- Benefits:
-
- Multi-layered protection with industry certifications.
- Simplified management with a user-friendly interface ensures that you and your team can navigate our solutions with ease, making your cybersecurity journey a smooth one.
Endpoint Detection and Response (EDR)
Offers robust detection and response capabilities, providing uninterrupted data visibility and control over system hardware, OS, and applications. It supports both cloud and on-premise deployments.
- Key Features:
-
- Multi-phase verification with behavioral analysis and ML-based detection.
- Automated and manual IOC lookup.
- Advanced notification system with SIEM integration.
- Benefits:
- Detects and blocks advanced attacks in real time.
- Reduces the need for external incident response firms.
- Provides thorough investigations with historical data search.
Enterprise Mobility Management (EMM)
A powerful tool for managing mobile devices running on Android and iOS. It allows organizations to control apps, monitor internet usage, track device location, and enforce policies.
- Key Features:
- App management, launcher, and kiosk mode.
- Comprehensive mobile security and anti-theft features.
- Virtual fencing and data monitoring.
- Benefits:
- Ensures data security beyond the corporate network.
- Provides real-time alerts on policy violations.
- Supports zero-touch enrollment for easy device management.
Zero Trust Network Access (ZTNA)
Provides secure remote access to corporate applications and services for employees, contractors, and vendor staff across borderless workspaces.
- Key Features:
-
- Identity management with integration to cloud IDps.
- Zero Trust policies with granular controls.
- Layer 7 firewall and DDoS protection.
- Benefits:
- Simplifies policy management with visual-first zero-trust for admins.
- Reduces complexity and enhances security with a user-centric access model.
- Supports both agentless and agent-based access options.
Why Seqrite?
- Comprehensive Protection
- AI/ML-Powered Technology
- Global Expertise in Cybersecurity
- Simplified Management for Ease of Use
- Enterprise-Grade Security at a Competitive Price Point
