Asset Intelligence & Security Domain
In the “borderless digital age,” where devices and networks transcend traditional boundaries, siloed asset management leads to limited device visibility and increased security vulnerabilities. To ensure effective asset management and security compliance, a comprehensive, real-time Asset Intelligence system is essential for gaining insights into assets and devices.
Unlock The Power Of Unified Asset Intelligence & Security
Truvisor joins forces with industry leaders to provide a comprehensive Asset Intelligence and security solution. By adopting a holistic approach to address the operational and security challenges for key components like Assets, Networks, End Points, Dashboards, and Automation, we help an organization achieve operations efficiency while bolstering security.
Protect Your Assets
See & Secure Every-Thing
An Agentless Device security platform is needed to safeguard all types of devices, including managed, unmanaged, IoT, OT, and cloud resources.
Key Benefits:
- Efficient Operation
- See and Secure all your device: Maintain asset visibility and classification.
- Accurate Inventory and adherence to compliance regulations.
- Simple to deploy and integrate: Ensure asset uptime during cyber attacks.
Enhanced Security
- Real-time monitoring and prompt detection of security threats.
- Accurate visibility of changing assets and new vulnerabilities.
- Seamless integration of all security tools.
Protect Your Network
Rapid Threat Detection and Response in Hybrid Cloud Environments
AI-powered solutions for comprehensive network traffic visibility, swift threat detection, and quick identification of attack sources to effectively secure network and hybrid cloud environments.
Key Benefits:
Operational Efficiency:
- Detect threats through comprehensive East-West traffic visibility.
- Gain security visibility tailored for hybrid cloud environments.
- Monitor network traffic effectively.
Enhanced Security:
- Real-time monitoring of patient zero attacks.
- Conduct proactive threat hunting with advanced tools and efficient processes.
- AI-powered automation to streamline incident response and compliance reporting.
Protect Your Endpoints
Comprehensive endpoint protection and effective patch management are essential to proactively defend against threats, maintain a strong security posture, and safeguard your organization’s data.
Next-Gen Patch Management
Next-Gen Endpoint Patch Management automates the patching and updating of software on endpoint devices. It enhances security and compliance, reduces vulnerabilities, and strengthens your overall security infrastructure.
Key Benefits
- Streamline endpoint hygiene through efficient inventory management and patching practices.
- Monitor endpoints in real-time for prompt threat detection and response.
- Manage vulnerabilities effectively by maintaining accurate inventory, prioritizing patching, and adopting a risk-based approach to software and hardware assets.
Unified Protection from Endpoint to Everywhere
NGAV, EDR, and XDR enable real-time threat detection, investigation, and response to stop malicious operations before they gain traction, eliminating the need to chase alerts.
Key Benefits:
Simplify Operation:
- Monitor, detect, and respond to endpoint activities with precision.
- Maximize the efficiency of valuable Security Operations Center resources.
- Detect and investigate sophisticated attacks with unmatched visibility.
Robust Security:
- Next-gen technologies for heightened protection against evolving cyber threats.
- Gain insights of MalOp™ incidents from initiation to resolution.
- Anticipate attacker behavior and actions through automated threat intelligence analysis.
Dashboard & Automation
AI-Powered Automated Threat Intelligence and Compliance.
Automate threat intelligence, achieve compliance and gain real-time security monitoring and response.
Key Benefits.
- Automated workflows and alerts for increased operational efficiency.
- Simplifies compliance management and audit reporting.
- Log and Event Management for visibility and threat detection.
- Automated Threat Response with predefined playbooks.
Act Now! Contact Us for a Complementary Security Assessment
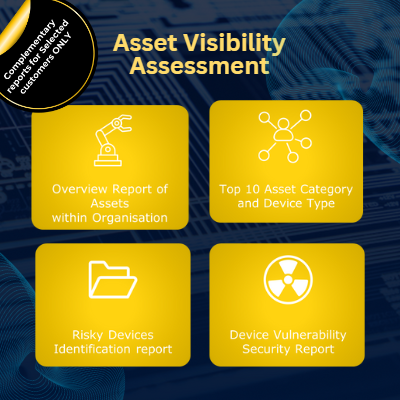
Asset Visibility Assessment
Complementary reports for “Overview Report of Assets within Organization”, “Top 10 Assets Category and Device Type”, “Risk Devices Identification Report” and “Device Vulnerability Security Report”
Industry Awards and Accolades for our Technology Partners