Cymulate
A Strong Defense Starts with the Challenge of Offense.

Continuously measures & conveys cyber effectiveness and risks to leadership.

Validates controls, find security drift & discovers emergent threat risk.
Prioritizes vulnerabilities & maps exposures to security frameworks.

Rationalizes cyber security spend & provides performance ROI trending.
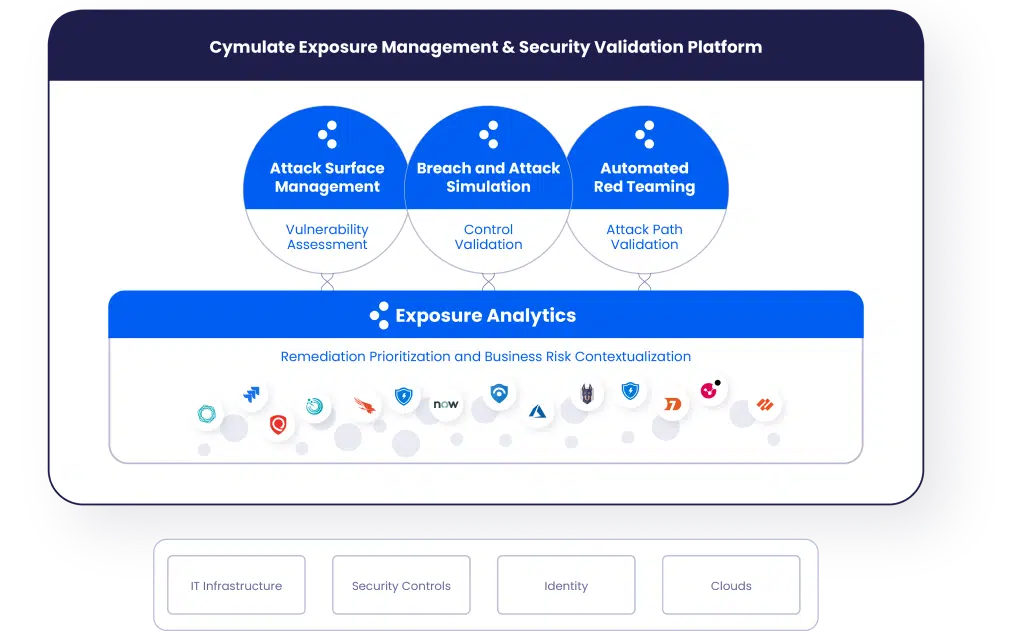
Cymulate Exposure Management and Security Validation Platform
Continuously challenge and validate cybersecurity posture while contextualizing and optimizing cyber resilience
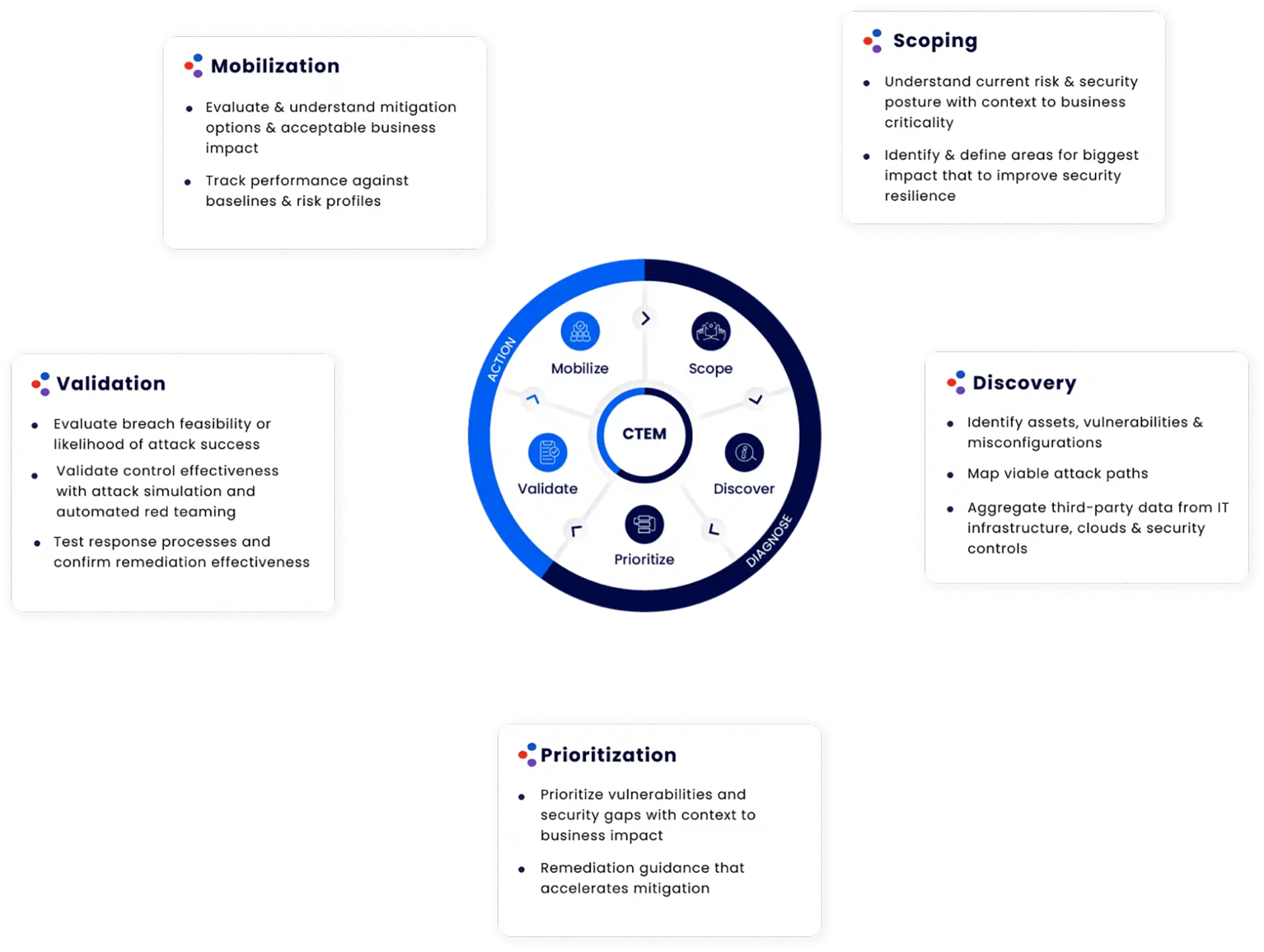
The Cymulate platform drives continuous threat exposure management programs and supports the technical and business requirements of scoping, discovery, prioritization, validation, and mobilization.
The Cymulate Platform Drives Continuous Threat Exposure Management Programs
Cymulate Attack Surface Management (ASM)
Discover attack surfaces, identify misconfigurations, and scan for vulnerabilities for more effective and efficient remediation programs.
-
- Internal & External Asset Discovery—Automate scans across on-prem, cloud, and hybrid setups. Detect systems, apps, interfaces, and domains without manual audits. Regular re-scanning is included.
- Vulnerability, Misconfiguration & Dark Web Scanning – Identify vulnerabilities, misconfigurations, and data exposure. Scan frameworks, libraries, domains, IPs, and devices, Includes dark web monitoring for potential threats.
- Unified Attack Path Mapping and Analysis—Rapidly map attack paths across networks, clouds, and identity systems. Identify and prioritize high-risk vulnerabilities based on exploitability for targeted defense.
- Actionable Reporting – Continuous reporting tracks drift and offers remediation guidance. Visualize attack data and quickly assess top threats, assets, and findings with detailed technical insights.
Breach and Attack Simulation (BAS)
Comprehensive security validation, measurement, and optimization for organizations of all sizes.
-
- Identify Exposure to Latest Active Threats – Continuous updates with new assessments for current and emerging threats.
- Validate Security Architecture Against APT Attacks—Test the entire stack of cyber controls against simulated full kill-chain APT attacks, from attack delivery to exploitation and post-exploitation.
- Comprehensive Dashboard—Data-driven breach simulations aid proactive risk management. The dashboard displays control health individually and collectively. An intuitive interface enables detailed analysis. Vendor integrations optimize efficiency and reduce risk. Straightforward remediation guidance is included.
- Simulation Scenarios – access real-world attack simulations based on known adversary tactics with over 120,000 ready-to-use templates. Customize attacks and execute assessments across the Cybersecurity Kill Chain.
- Actionable Reporting – Streamline risk management with detailed reports, collaborative Red, Blue, and Purple Team efforts, executive insights, and MITRE ATT&CK® mapping. Customizable dashboards aid decision-making.
- Mitigation Guidance offers mitigation strategies for identified gaps, diverse remediation options, and support for data sharing through SIGMA. It is integrated with EDR/XDR, SIEM, and SOAR tools for targeted actions.
- MITRE ATT&CK® Reporting—Reports align with the MITRE ATT&CK® framework, with custom scenarios mapped to tactics and techniques. Heatmaps visualize strengths and weaknesses.
Cymulate Continuous Automated Red Teaming (CART)
Safe and automated red teaming allows for more testing, more often with existing staff.
-
- Network Pen Testing – Safely test threat tactics, validate against security controls, and analyze network and endpoint defenses for accurate assessment and detection.
- Full Kill-Chain Assessments automate security testing with real-world cyber attacks, including email targeting with safe payloads simulating various threats, ensuring controlled execution.
- Phishing Awareness – Assess employee resilience to phishing via actual attacks, record interactions, and pinpoint training needs and policy adherence.
- Actionable Reporting – Share insights, assess security posture with technical and executive reports, and customize dashboards mapped to MITRE ATT&CK® and other frameworks.
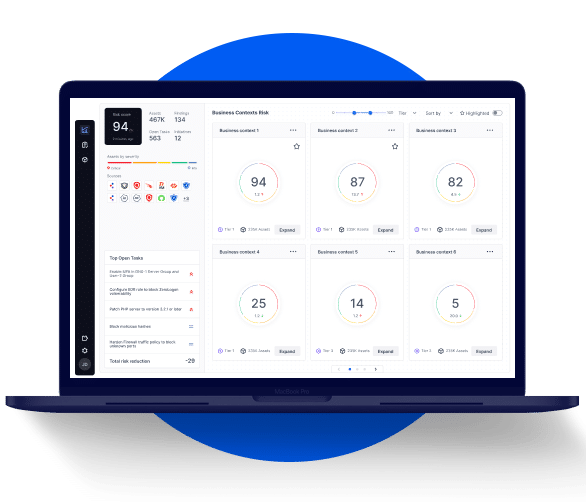
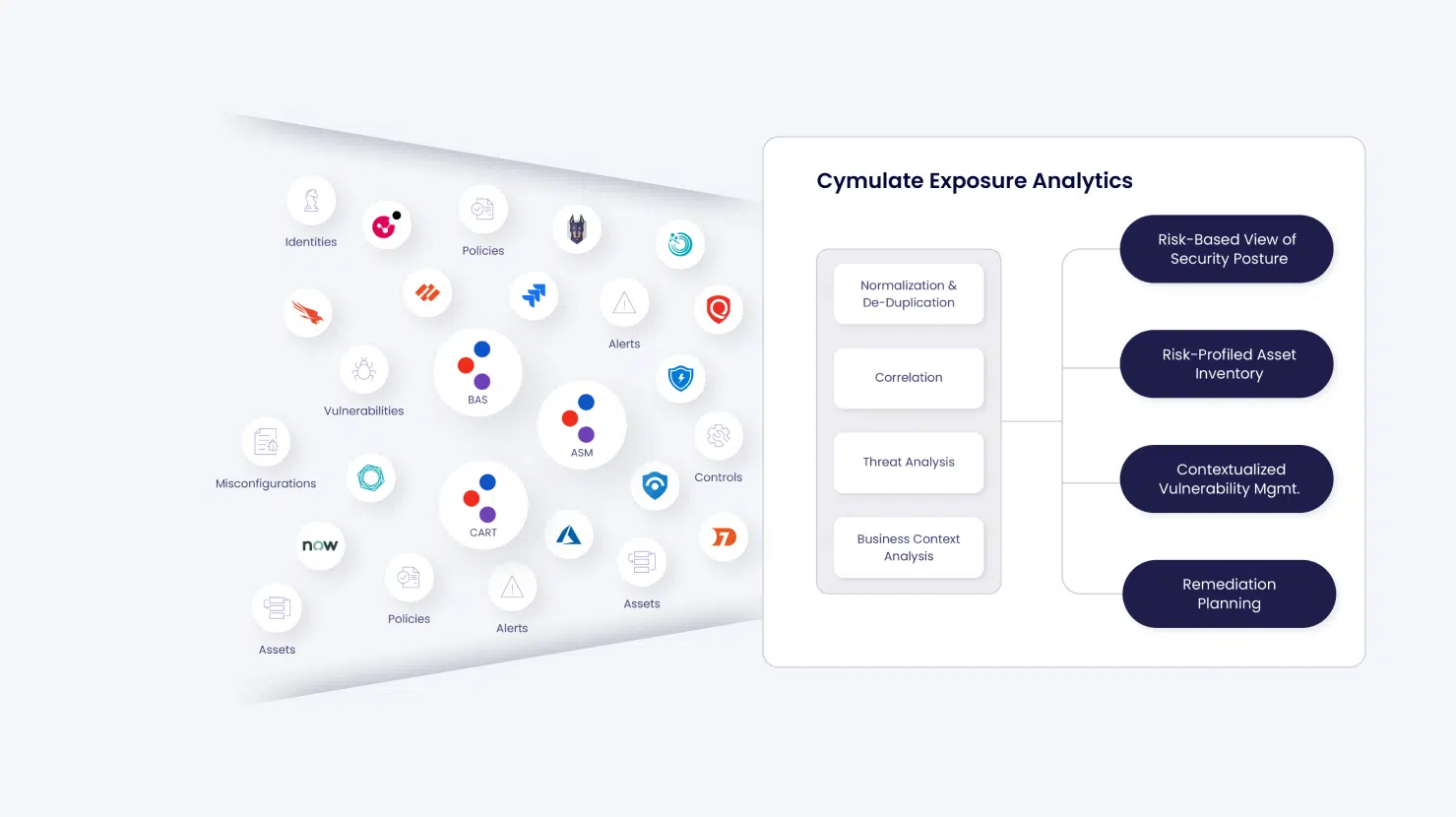
Exposure Analytics
Ingest and correlate data from vulnerability management, security validation, and other data sources to establish a baseline and optimize cyber resilience.
-
- Measure and baseline Cyber Resilience . Quantify risk based on attack surface, business impact, control efficacy, and breach feasibility, as well as external data such as CVSS scores and threat intel.
- Profile Assets for Risk and Business Context – Aggregate and contextualize data from various sources to provide a comprehensive asset view, including security controls, policies, vulnerabilities, and mitigation status.
- Focus on the Greatest Risk And Mobilize Mitigations With a Clear View of Impact– Prioritize mitigations that deliver the most significant risk reduction and improve cyber resilience.
- Accelerate Mitigation with Remediation Planning—Mobilize teams to take action with a complete understanding of a vulnerability’s operational and business impact.
Cymulate Gives You Confidence.
Cymulate’s security posture management platform offers continuous, automated solutions, empowering cybersecurity professionals with data-driven insights for informed decision-making.